Honeypot Moments: Accidentally Getting a VPN Providers IP.
I run a number of Cowrie honeypots hooked up to Graylog, and sometimes take a look at the data for weird shit.
I probably will pick the weirdest thing of the week and make a specific blog post about it, writing it up at the weekend. No guarantees on how often I remember to do this.
I also have a writeup in the works on how I set up the whole thing - it took me less than an hour or so to do.
Anyway, I couldn't resist noting this fucking nonsense.
I was faffing around sorting by the most common credentials when I spotted this.
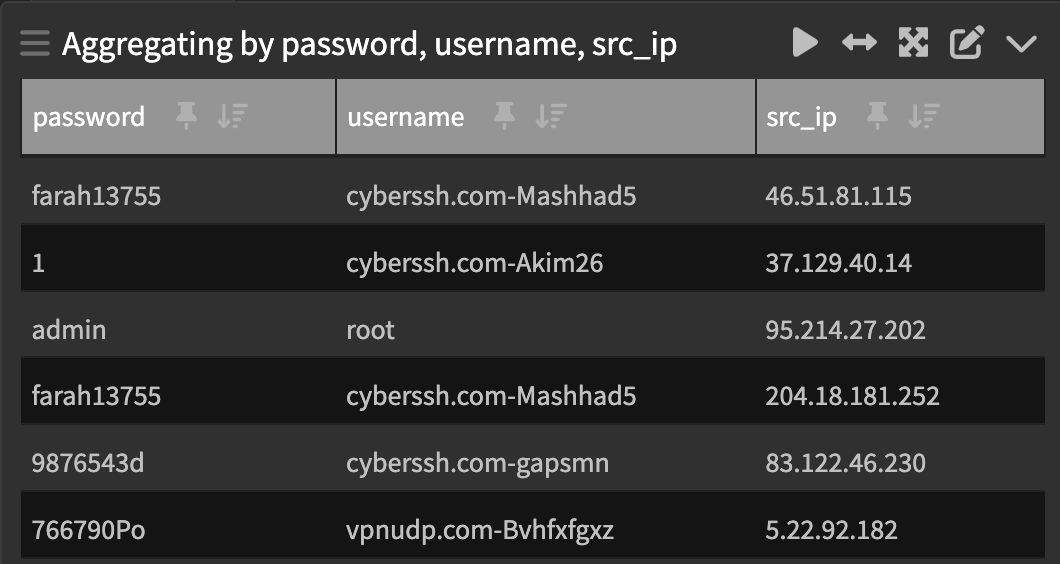
A search on the top source IP landed me this... He just keeps trying to log in.
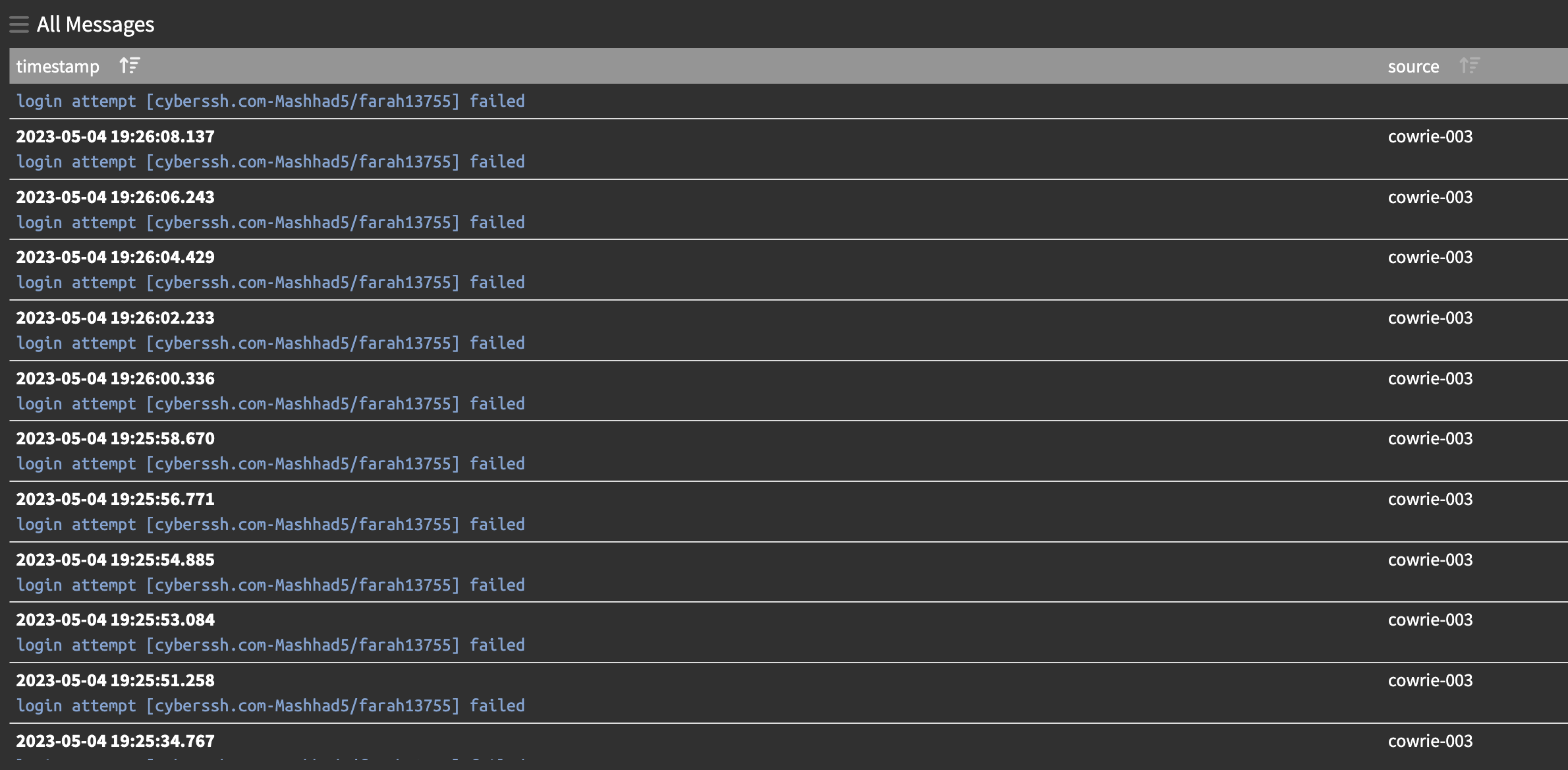
$ cat cronman.csv | wc -l
2446
$ head -n 5 cronman.csv
"timestamp","source","message","src_ip"
"2023-05-04T07:00:09.991Z","cowrie-003","login attempt [cyberssh.com-Mashhad5/farah13755] failed","46.51.81.115"
"2023-05-04T07:00:11.969Z","cowrie-003","login attempt [cyberssh.com-Mashhad5/farah13755] failed","46.51.81.115"
"2023-05-04T07:00:13.957Z","cowrie-003","login attempt [cyberssh.com-Mashhad5/farah13755] failed","46.51.81.115"
"2023-05-04T07:00:15.966Z","cowrie-003","login attempt [cyberssh.com-Mashhad5/farah13755] failed","46.51.81.115"A quick check of the top few guys there (the cyberssh and vpnudp ones) show me they are all trying to connect from Iran.
They also tend to be trying with high frequency, indicating some kind of cronjob or client software desperately trying to reconnect to a server whose IP I now possess.
A little digging shows me vpnudp and cyberssh are VPN providers that look the same.
Compare:
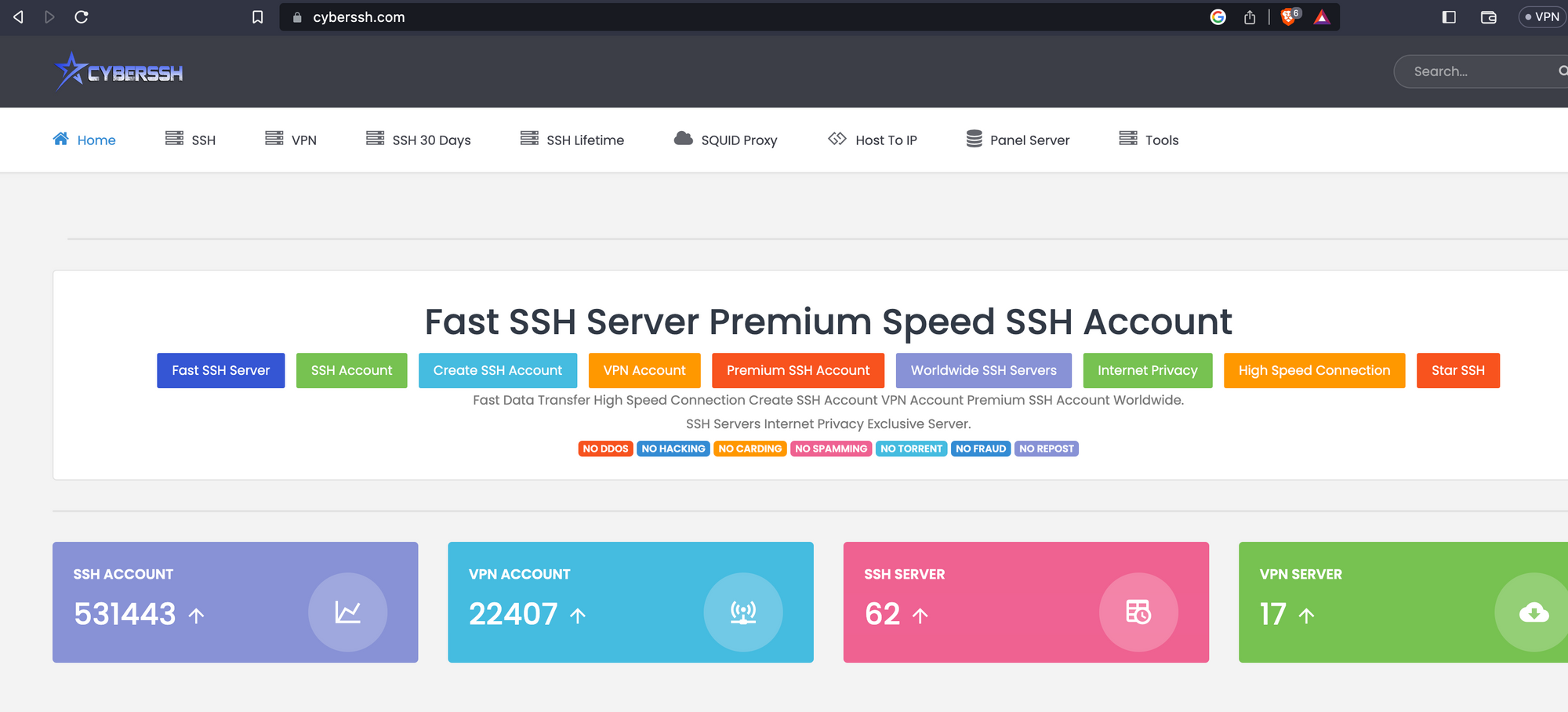
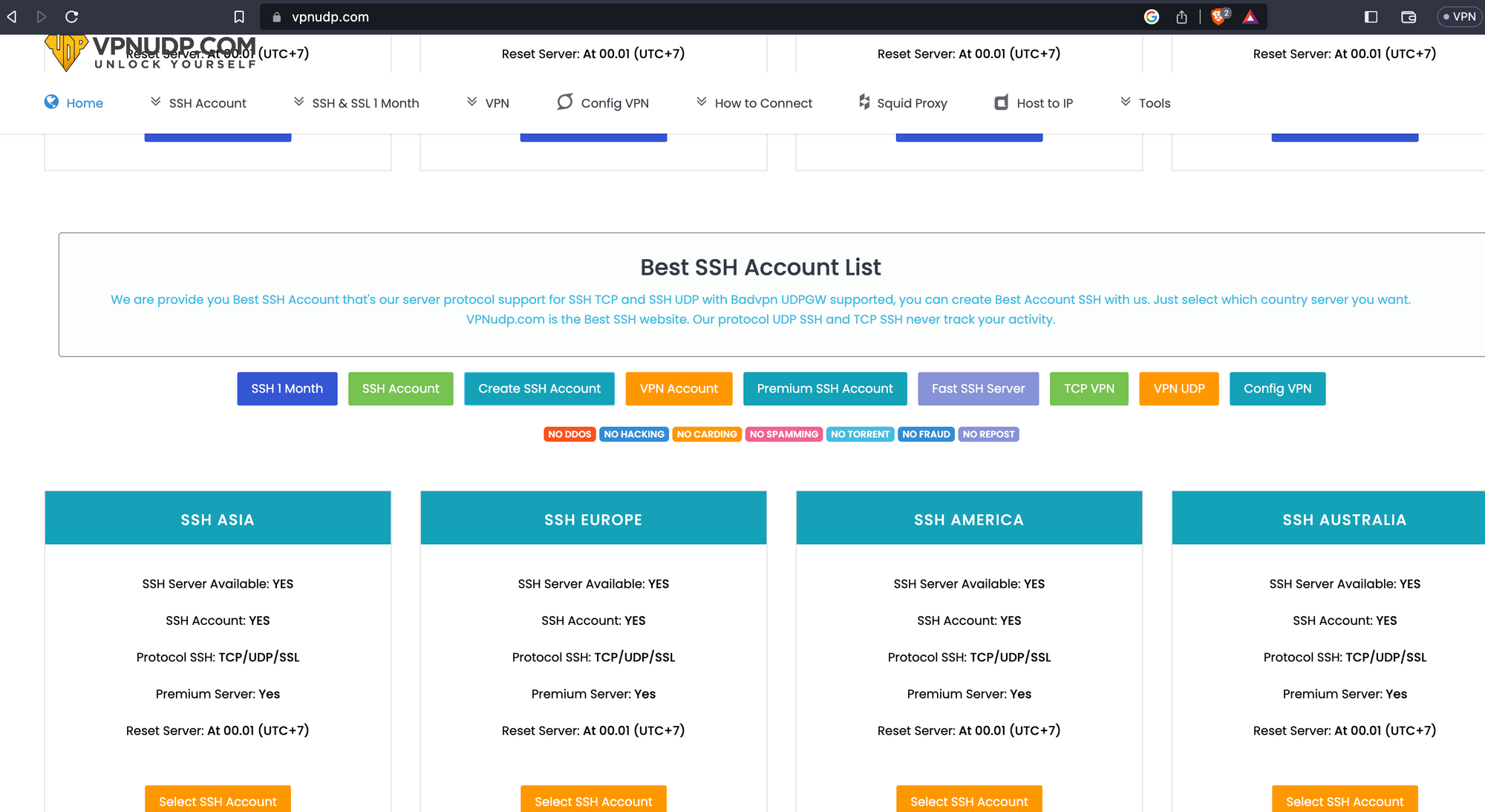
Extremely similar looking, no?
Further mining in the data gave me a list of cyberssh usernames:
cyberssh.com-0223
cyberssh.com-0423
cyberssh.com-0430
cyberssh.com-Akim18
cyberssh.com-Akim26
cyberssh.com-Amin9
cyberssh.com-Bbgghjjb
cyberssh.com-Fffgfss
cyberssh.com-Hamid44
cyberssh.com-Mashhad5
cyberssh.com-MjI1NjYK51
cyberssh.com-MjI1NjYK52
cyberssh.com-Moiztra
cyberssh.com-Ndhufv
cyberssh.com-bbgghjjb
cyberssh.com-esraresra
cyberssh.com-gapsmn
cyberssh.com-gsm1
cyberssh.com-gsm2
cyberssh.com-mahdy
cyberssh.com-mahdy4
cyberssh.com-mansjd
cyberssh.com-reihan1
cyberssh.com-spn1
cyberssh.com-spnu1
cyberssh.com-spnuk1
cyberssh.com-ss3987gf5513
cyberssh.com-u1
cyberssh.com-u2
cyberssh.com-yegane24020And passwords:
1
110128
1234
12345
123456
1234567
147075
9876543d
9876543s
987654fd
999999999
bbhgg765556
drftgtedf
farah13755
hvth7544I then ran a quick search on ipinfo by putting all the IP's through a disgusting bash oneliner using their API, to see which countries I was getting. It was primarily Iran, with some American, German, Turkish and Chinese IP's showing up. Neat.
I then decided to do the same search on vpnudp users...
vpnudp.com-0205uk
vpnudp.com-10ord650
vpnudp.com-Bvhfxfgxz
vpnudp.com-bcfdt
vpnudp.com-redhackV
vpnudp.com-rjiejwe3And passwords:
<blank>
0205
123456
766790Po
gdhfut
jsnfkslUEWIFH4R2
redhackV
redhackVredhackVredhackVredhackVThe vpnudp users came primarily from Iran, with Thailand and the US also showing up. Neat.
In conclusion here, what seems to have happened is the IP I was assigned for my honeypot at a certain cloud provider, is an IP address that was previously being used by these VPN providers.
And it seems these providers never pushed out updates to their customers, leaving me in the weird position where their customers are trying to proxy through my honeypot, leaving me in a position for "upstream collection" if I was so inclined.
Really makes you wonder how good some of these VPN providers are at security, eh?
Footnote: As a friend of mine, Lauri, pointed out - this also implies that the CyberSSH/VPNUDP users client nonsense is not doing any kind of SSH host key verification or pinning, which really makes me curious about their security practices.